ABT - Issue 2025-01-22
Federal Police Operation CHAES | Fraud involving Pix payment method | Google Ads Phishing with… Google Ads
Federal Police launches Operation CHAES
On January 22, Brazil Federal Police (PF) has launched an operation against the developers of CHAES malware, also known as Chae$. Unlike most PF operations, this one didn’t make use of the force’s creative department - the operation name is just Operação CHAES.
The press release was very brief, with just a technical overview and no attribution information whatsoever. Morphisec researchers chose to attribute the malware to Lucifer (blog name) and lucifer6 (identifier found in communications with C2. The only information disclosed in the press release was the location of the arrests - Campinas, SP and Caldas Novas, GO.
This malware was first observed and described by Cybereason Nocturnus Team, in November 2020. In that occasion, the team published a Threat Overview and a 29-page paper in PDF, full of indicators.
In January 2022, AVAST shared the results of their own analysis of CHAES samples observed in Q4 2021. In December 2022, brazilian threat intelligence company Tempest published an analysis on a new CHAES campaign. Finally, in 2023 (PDF) and 2024 (PDF) Morphisec published a reports on observations of Chae$, including a shoutout to researcher Arnold Osipov (Morphisec). This is not the first shoutout: in February 2022, the developers of Chae$ published a blog post in response to AVAST blog post.
Initially, the main target of CHAES was MercadoLivre and MercadoPago, its own payment method. MercadoLivre is the largest e-commerce company in Latin America, similar to eBay and with its own logistics structure.
The main malware capabilities were Credential Stealing, Screen Capture, Browser Monitoring and Reconnaissance. The malware is delivered in multiple stages - six according to Tempest - and make use of Lolbins and legitimate software, making it challenging to detect with traditional Antivirus methods. Multiple programming languages (Javascript, Vbscript, .NET , Delphi, Node.js) is another effort that shows the concern of developers in making this malware stealth. No vulnerabities were exploited - the final payload of CHAES is a Node.js information stealer.
This is one example of brazilian-style Living Off the Land (LOTL) or LOLbin strategy. All research above contains IOC, please refer to the resources for the latest indicators. However, please note that malware that relies on LOTL is more effectively contained with Indicators of Attack (IOA). Good references on IOA were shared by CrowdStrike, SentinelOne and Splunk.
Google Ads Phishing with… Google Ads
On January 15, Malwarebytes reported a malvertising operation they consider the most egregious that they ever tracked. Criminals were observed collecting credentials from individuals and organizations which advertise using Google Ads in phishing campaigns that used fraudulent Google Ads. The goal was to collect Google Account credentials.
What caught my attention about this particular article is the attribution section. Malwarebytes found evidences that tie this threat to two teams, one based in Asia and another based in Brazil. More than 50 fraudulent ads were attributed to the Brazilian team. The evidences are basically comments in the JavaScript code of the phishing kit, with Brazilian Portuguese.
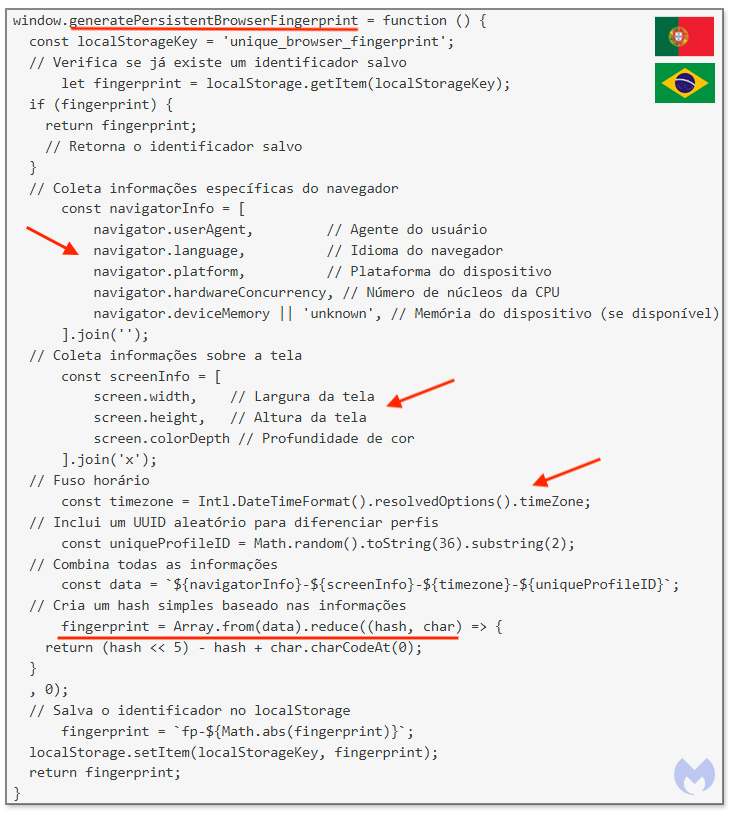
Malwarebytes article include a long list of IOC. Please refer to that blog post for the latest indicators.
Pix or it didn’t happen
Brazilian financial system is very mature, as you might have heard here and there. It really is. I felt proud for that for many years visiting Europe and the U.S. when I saw lousy bank security that would not stand Brazilian criminals. Chip and PIN cards were first introduced in 1999, Internet banking was introduced in 1996. Since then, many strategies were used, including, but not limited, to registration of desktops, hardware authenticators, SMS authentication, proprietary anthenticators based on mobile apps, multiple annoying passwords and even endpoint software like Warsaw by TOPAZ Stafanini [1,2] that resembles a rootkit. All in the name of security.
For decades, the primary method of paying bills was boleto, a payment order that contains a long code with a barcode representation. This is still how most brazilians pays the school of kids or utilities. Boleto fraud is still strong in Brazil, particularly in phishing.
The game started to change with the introduction of digital banks, based primarily on mobile applications. In 2013, Nubank started its operations, followed by INTER in 2015 and many others. Between that time and the Pandemic in 2020, digital banks developed and took place of desktop banking. Most Brazilians don’t even own a desktop. Attackers had to adapt.
Then came Pix, taking place of DOC and TED money transfer protocols. Pix is a very sophisticated instant payment (IP) system indroduced by Banco Central do Brasil (BCB) in 2020 in constant change in response to the hostile environment of Brazil.
With Pix, came many other challenges. It was no longer necessary to assault bank clients on ATM - the ATM was in the pocket of every Brazilian. Pix became widely adopted, mainly because it is very easy to use and wothout transaction fees, unlike the old DOC and TED protocols. Also, payments made using Pix avoid the fees of credit and debit cards transactions, making this payment method very attractive for business owners of any size. Pix, combined with the proliferation of digital banks, practically erradicated the cash in Brazilian wallets in a matter of five years. Credit and debit cards never achieved that in the country.
This week many news outlets replicated an ACI Worldwide report, 2024 Scamscope The Battle for Trust (PDF). Nothing changed recently, most likely this is just the result of a well done press release process and impressive numbers. This is ACI’s conclusion for Brazil:
While Brazil has made significant strides in tackling APP fraud, the battle is far from over. Real-time payment systems are a vital part of the modern economy, but they come with inherent risks that require constant monitoring and innovative solutions. BACEN’s new regulatory framework, combined with greater industry collaboration and the use of cutting-edge technology like AI, offers a path forward. As scam tactics evolve, so too must the systems designed to protect Brazilian consumers.
All major news outlets published articles about that. Isto É magazine and CNN Brazil focused on the R$ 11-12 billion figure (projected loss until 2028), while Veja magazine focused on the reasons why people fall victim of Pix fraud.
Found mistakes or just would like to report something for the next edition? Reach out to me over Substack or @ronaldotcom at Blue Sky.